Everlaw Blog
See what’s new at Everlaw and read the latest and greatest in legal tech and ediscovery.
See what’s new at Everlaw and read the latest and greatest in legal tech and ediscovery.

5 min read

Former Executive within Internal Revenue Service Criminal Investigation on change management in the public sector.
6 min read

Dr. Megan Ma discusses large language models and the role of generative AI in the law.
2 min read

Key provisions and their potential implications for government attorneys.
2 min read

The mind behind ‘Hidden Brain’ speaks on the unconscious patterns that drive human behavior at Everlaw...
2 min read
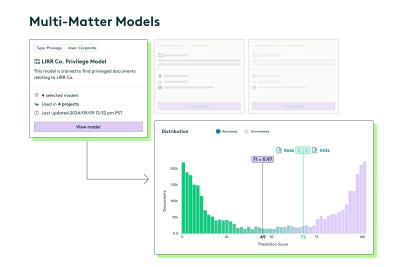
Everlaw's Multi-Matter Models lets legal teams apply previously trained predictive coding models to new cases.
3 min read

Judge Scott Schlegel has helped create one of the most technologically-advanced courtrooms in the country.
12 min read

Learn strategies and solutions for effectively managing large-scale litigation in the public sector.
5 min read

HP uses Everlaw to tame litigation costs fueled by a proliferating of corporate data.
4 min read

Bringing technology into the courtroom is essential to keep the legal system at the forefront of...
4 min read

Steve Davis, VP of Forensics & Investigations at Purpose Legal, on the biggest forensics changes, challenges,...
6 min read

The top ediscovery certification programs in 2024 can help advance your career.
4 min read

See how the San Francisco District Attorney's Office responds quickly, acts securely, and increases efficiency with...
7 min read

Federal agencies need a trusted ediscovery partner to perform at their best.
2 min read

Following these legal holds best practices reduces the risk of adverse legal outcomes, sanctions, and penalties.
5 min read

Mark your calendars for October 22-24, 2024!
1 min read

Judge Bridget McCormack spoke with Everlaw about access to justice, generative AI, alternative dispute resolution, and...
14 min read

Allensworth uses Everlaw to get to the truth, faster.
3 min read

What the federal government's new executive order on AI means for public sector legal professionals.
5 min read

Juanita Luna discusses navigating change management as Legal Ops Director at PG&E.
6 min read

An ediscovery software RFP can help in finding the best provider for your organization's needs.
5 min read

The Second Circuit weighs in on AI use (and abuse) in the courts.
3 min read
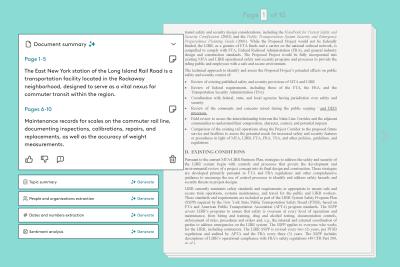
The latest releases from Everlaw help legal professionals realize the efficiency of generative AI.
4 min read
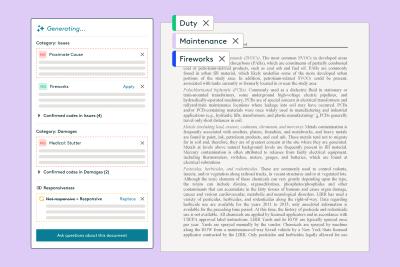
Prompting is key to maximizing the responses of large language models.
5 min read

Key TAR case law from recent years.
28 min read

AI document review is revolutionizing the legal industry.
4 min read

Investigations teams walk a fine collecting complex data and privacy concerns. Our distinguished speakers share tips.
4 min read

Bates numbering helps legal teams stay organized and on track.
4 min read

Strategies for getting ahead of the AI-driven surge in FOIA requests.
5 min read

Adams and Reese looked to Everlaw to transform their ediscovery program.
3 min read

Connect with Everlaw at Legalweek 2024.
2 min read

Everlaw CLO Shana Simmons discusses a model for corporate GenAI policies with FICO's Scott Zoldi.
3 min read
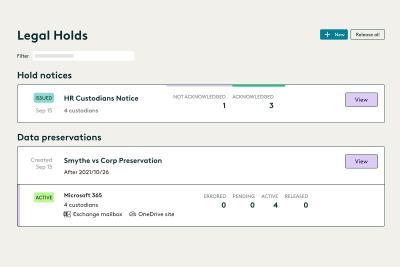
Understand Office 365 litigation hold basics and best practices and the modern legal hold tools available...
5 min read

Judge Paul Grimm speaks about the impacts of generative AI in the legal system.
13 min read

You can't prevent every attack, but you can prepare with these 4 tips.
4 min read

Managing ediscovery costs is more important than ever in 2024.
5 min read

The proposed rule change by the Fifth Circuit Court of Appeals could have far-reaching consequences for...
3 min read
Can you understand 365 days in just three numbers?
2 min read

The articles that resonated most in 2023.
6 min read

Well-planned and well-executed depositions can literally make your case in court.
13 min read

Keep up with emerging technologies and connect with peers at one of these 2024 legal tech...
3 min read

Gordon Calhoun discusses the future of generative AI and its influence on the legal profession.
4 min read

GenAI will usher in a renaissance for lawyers and legal ops professionals, and roll out unique...
6 min read

Experts share tools and techniques to help optimize the cost and accuracy of the ediscovery process.
3 min read

Everlaw founder and CEO AJ Shankar reflects on a year of GenAI innovation.
6 min read

The press found our latest in-house counsel survey compelling. See the highlight reel.
4 min read

See the three attitudes successful corporate law departments cultivate in the quest for true partnership with...
3 min read

GenAI was on everyone's minds at Everlaw Summit '23.
5 min read

Judge Paul Grimm and Dr. Maura Grossman speak on AI and its implication on the American...
5 min read

Celebrating leaders who are driving breakthroughs across their organizations and the profession.
3 min read

Strategy is everything when it comes to the successful implementation of any new technology. Here are...
4 min read

Creating a more equitable hiring process in the legal profession.
3 min read

A new hire attends Everlaw Summit '23 and takes note of all the exciting change and...
3 min read
See how in-house legal professionals rate collaboration and transparency with their partners in this new survey...
3 min read

At Everlaw Summit, Patrick Radden Keefe shares the hidden story behind the nation’s opioid crisis.
5 min read

GenAI is here to stay. Understand this transformative technology with Everlaw founder and CEO AJ Shankar.
9 min read

We've combined learning, guided practice, & verification so you can leverage your ediscovery software to its...
3 min read

Modern tech solutions let users handle the full legal holds process with much more ease, starting...
2 min read

Don't miss out on one of the best legal events of the year.
1 min read

What the best legal teams are doing today to ensure success in litigation and investigations.
3 min read

SunPower's Brad Johnston discusses building bridges between in-house legal and the business.
6 min read

Practitioners specializing in ediscovery from various state attorney general offices shared their tips.
3 min read
72 and 40: Two numbers tell the story of the legal profession at the dawn of...
3 min read

Paralegals play an essential role in helping their legal teams best find the data that can...
3 min read

Best-selling author and investigative journalist Patrick Radden Keefe to keynote Everlaw Summit '23.
2 min read

Learn how we're bringing the power of generative AI to litigation and investigations.
8 min read

Get product certified in-person with Everlaw's Reviewer and AI certifications at Everlaw Summit 2023!
1 min read

This October, we're bringing together some of the best in the profession. The Everlaw Summit awards...
2 min read

As AI takes the world by storm, litigators discuss real-life examples of its use in the...
4 min read

The explosion in new data types is driving adoption of cloud connector technologies designed for faster...
4 min read

See how Everlaw is exploring generative AI capabilities in a way that is responsible, thoughtful, and...
4 min read

Real-time collaboration tools accelerate and improve results. Here's how.
4 min read

See why Everlaw ranked #1 in multiple reports from G2, the industry-leading, peer-to-peer review site.
2 min read

See how this Am Law 50 firm uses modern technology to become a leader in innovation,...
4 min read

Everlaw Summit Awards are a celebration of legal professionals staying ahead of the curve.
2 min read

As AI eats the world, here are practical use cases from the floor of the CLOC...
3 min read

Learn how Everlaw is delivering responsible generative AI to our customers.
2 min read

Six months into the ChatGPT era, legal professionals are actively investigating generative AI's potential impact on...
3 min read

Google’s Meghan Landrum and Ironclad’s Chris Young share their approach to in-house digital transformation.
5 min read

The need is acute. The technology is here. The change-enablers are ready to go. See why...
3 min read

How Everlaw and the Leadership Council on Legal Diversity are working to build a more diverse...
3 min read

Here are four steps you can implement to protect yourself and your client information.
4 min read

Investigations teams backed by the right technology make better informed strategic decisions at every step of...
6 min read

Leaders from Google, Everlaw, and Ironclad discuss the modernization of in-house legal.
5 min read

AI was in the air at Legalweek. The consensus? AI might not replace lawyers, but lawyers...
3 min read

Harness IP's Penny Jones-Magee discusses her firm’s approach to ediscovery and the impact of choosing a...
2 min read

Dive deep into the important work UCSF is doing by making millions of opioid litigation documents...
4 min read
Everlaw announces three new features, designed to help legal professionals unearth the stories hidden between the...
5 min read
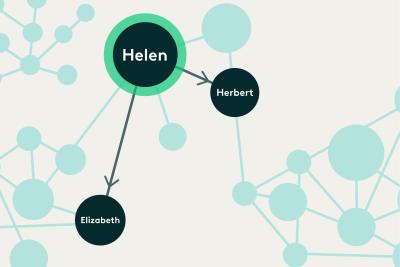
What if, instead of reading thousands of files to understand key players, we could see them...
4 min read

The great stagnation has come to an end, and the move to modern ediscovery is here.
4 min read

It’s clear that the legal teams using AI in their litigation and investigative work will gain...
4 min read

Everlaw's Director of Legal Ops & Strategy explains how to successfully ease cross-functional teams into new,...
7 min read

Meet Everlaw at Legalweek 2023 and empower your teams with the most advanced technology for ediscovery...
3 min read
See how Barnes & Thornburg, an Am Law 100 firm, transformed its approach to ediscovery with...
1 min read

See how this nonprofit is centralizing and streamlining the legal team’s mission-critical work.
5 min read

The time to lay the foundations for effective ediscovery is before you get hit by a...
7 min read

7 min read
3 min read

4 min read

1 min read

5 min read

3 min read

Why you should consolidate your discovery workflows into one platform for every step, from legal holds...
5 min read

Former Executive within Internal Revenue Service Criminal Investigation on change management in the public sector.
6 min read

Dr. Megan Ma discusses large language models and the role of generative AI in the law.
2 min read

Key provisions and their potential implications for government attorneys.
2 min read

The mind behind ‘Hidden Brain’ speaks on the unconscious patterns that drive human behavior at Everlaw...
2 min read

Everlaw's Multi-Matter Models lets legal teams apply previously trained predictive coding models to new cases.
3 min read

Judge Scott Schlegel has helped create one of the most technologically-advanced courtrooms in the country.
12 min read

Learn strategies and solutions for effectively managing large-scale litigation in the public sector.
5 min read

Vice President of People, Leah Fine, discusses her passion for leading teams.
3 min read

HP uses Everlaw to tame litigation costs fueled by a proliferating of corporate data.
4 min read

Bringing technology into the courtroom is essential to keep the legal system at the forefront of...
4 min read

Steve Davis, VP of Forensics & Investigations at Purpose Legal, on the biggest forensics changes, challenges,...
6 min read

The top ediscovery certification programs in 2024 can help advance your career.
4 min read

See how the San Francisco District Attorney's Office responds quickly, acts securely, and increases efficiency with...
7 min read

Federal agencies need a trusted ediscovery partner to perform at their best.
2 min read

Following these legal holds best practices reduces the risk of adverse legal outcomes, sanctions, and penalties.
5 min read
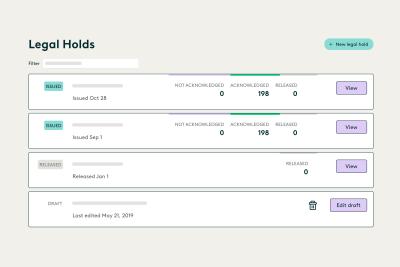
With litigation on the horizon, legal holds are essential to a defensible ediscovery process.
4 min read

Sean Hert shares how technology is shaping the future of legal support and transforming the work...
4 min read